3 Key Strategies for Securing SAP Business Data Cloud

Chapters
Share Article
Let's Talk SAP Security
Have questions about SAP Security? We’re here to help. Contact Us
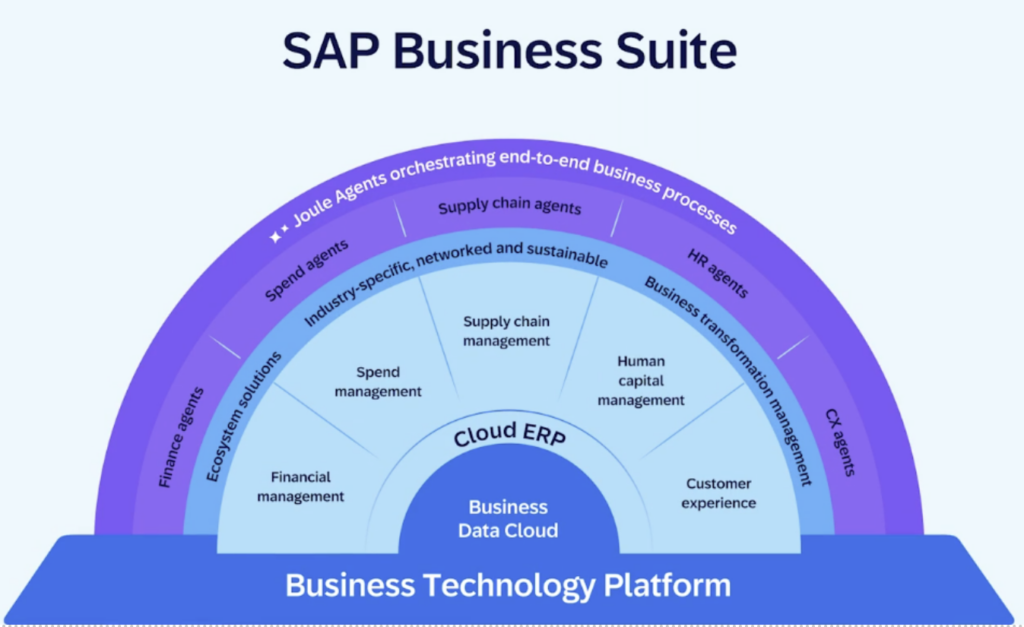
The recent announcement of SAP Business Data Cloud marks a significant milestone in enterprise data management. This innovative solution, developed in collaboration with Databricks, aims to unify and govern all SAP and third-party data, providing a trusted foundation for impactful decision-making and reliable AI. As organizations increasingly rely on data to drive their operations, protecting this asset becomes paramount. This article explores the key strategies to safeguard SAP Business Data Cloud on top of the SAP Business Technology Platform (SAP BTP) and at the core of Cloud ERP.
Understanding the Technology Stack
SAP Business Data Cloud integrates several advanced technologies to deliver a seamless data management experience. At its core, it combines SAP Datasphere, SAP Analytics Cloud, and SAP Business Warehouse with the new SAP Databricks, creating a unified platform for data engineering, machine learning, and AI workloads. The solution also supports an open data ecosystem, integrating with data and AI partners like Collibra, Confluent, and DataRobot. This technology stack provides the foundation for a secure and scalable data environment.
Key Strategies for Protecting SAP Business Data Cloud
1. Continuous Monitoring and Threat Detection
Continuous monitoring and threat detection are essential for identifying and mitigating potential security threats. To detect anomalies, trigger alerts, and provide actionable insights to prevent security incidents, SAP customers should activate a security shield around their SAP Business Data Cloud based on a template of pre-configured rules that leverage built-in SAP Security knowledge. The SecurityBridge Threat Detection has hundreds of listeners configured and active out-of-the-box to detect known attack vectors and malicious activities within your SAP Business Warehouse or your applications based on SAP BTP. In addition, it leverages an anomaly detection engine for zero-day threats and gets instant updates pushed from the SecurityBridge Cloud in case of new critical SAP vulnerabilities. Ideally, SAP customers leverage an SIEM for SAP that bridges between a mature SAP Threat Detection and Response process on the SAP operations level and the overall IT security process on the enterprise level. SecurityBridge sends only pre-filtered events correlated to decision-enabling messages to the SOC team, so they can effectively respond to cyberattacks. This keeps the SIEM operations cost low and delivers know-how where needed.
2. Compliance and Security Enforcement
Ensuring compliance with industry regulations and standards such as GDPR, NIST or NIS2 is critical for maintaining data integrity and trust in the SAP Business Data Cloud. Organizations should perform regular vulnerability assessments and security audits to evaluate their data environment’s security posture. Each regulation has its own set of requirements, making it challenging to ensure comprehensive compliance and governance across all systems.
A good starting point is the SAP Security Baseline which is regularly updated by SAP. It contains minimal recommendations for secure settings in SAP environments. Addressing identified vulnerabilities promptly can help mitigate risks and enhance overall security.
The SecurityBridge baseline contains all best practices for hardening SAP systems and environments, like SAP BTP. These best practice recommendations are presented as a regularly updated Security Roadmap for SAP with ranked findings based on balancing between exploitation risk and resolution complexity. Starting with the “low hanging fruits” that have a high risk but can be mitigated easily, the roadmap also provides all necessary details for decision-making and the recommended parameter values.
With these, SAP operations teams are on the best track to harden their SAP environments and ensure regulatory compliance. The Security Dashboard for SAP provides instant access to all necessary information about the current state of the SAP Security posture and vulnerability rating.
3. Access Control and Identity Management
Implementing robust access control mechanisms is crucial for preventing unauthorized access to data. Role-based access control (RBAC) and attribute-based access control (ABAC) can help define and enforce policies that restrict data access based on user roles and attributes. Identity management solutions like SAP Identity Authentication Service (IAS) and SAP Cloud Identity Access Governance (IAG) help further enhance security by ensuring that only authorized users can access sensitive data.
Ensuring timely provisioning and de-provisioning of users to reflect changes in employment status or role changes is essential to maintain security. Managing access at different levels, like global accounts and subaccounts, requires a clear understanding of the hierarchical structure and appropriate delegation of administrative rights.
The SAP Business Data Cloud (BDC) is built upon SAP BTP and combines many of the services of this platform. The SecurityBridge Platform comes with built-in SAP Security expertise that helps SAP administrators navigate through the SAP BTP user role hierarchies and efficiently review the granted access rights and privileges.
Out-of-the-Box, SecurityBridge automatically executes all critical checks SAP recommends for strong authentication and robust User & Identity Management in SAP BTP, like activated MFA, disabled Social Sign-On, or the periodic review of users with administrative or other elevated privileges. Closely monitoring inactive users, especially external ones, also helps reduce the attack surface.
Conclusion
As SAP Business Data Cloud ushers in a new era of enterprise data management, protecting this asset becomes increasingly important. By implementing robust security measures, such as continuous monitoring, compliance, and robust access controls, organizations can safeguard their data and unlock the full potential of their AI and analytics capabilities. In doing so, they can drive innovation, make more impactful decisions, and maintain the trust of their stakeholders.
Are you interested in learning more about adopting an All-in-One Security Platform for SAP as the fastest and most efficient way to a mature SAP Security posture?
Contact us and we will be happy to tell you more about our guided approach to SAP Security excellence. For more SAP security-related news, articles, and whitepapers, please follow us on LinkedIn!