Is your SAP Solution Manager truly Cyber-Resilient?

Chapters
Share Article
With S/4HANA seeming to use up all the oxygen in the room, I want to call your attention to a non-S/4HANA system facing one of those SAP 2027 deadlines. As you may be aware by now, the 2027 deadline is not only for ECC, but ALSO for anything running on SAP NetWeaver 7.5 platform or lower. When I hear this, I think of many systems, but one of the most important is the SAP Solution Manager system.
Why Protect Solution Manager now?
💡 It connects to almost every other SAP system... ideal entry point for a threat actor!
In my June article on BW/4HANA Cyber-Resilience, we discussed that the most important system to protect is your S/4HANA system since it is the “system of record” for so much data… we followed the data from there, as it flowed downstream to BW/4HANA.
This month we focus on another important “supporting actor” to the S/4HANA “star of the show”. Consider the cybersecurity relationship between S/4HANA and SAP Solution Manager. Which system handles the upgrades, transports, daily operations, and monitoring going into S/4HANA? It is, in many cases, the Solution Manager system. And, if that SAP Solution Manager system is compromised, then ANY and EVERY system that is connected to it might be at risk from an attacker’s “Lateral Movement” from Solution Manager into other SAP systems.
Think about the historical account of the Trojan Horse. The Gift, an oversized wooden horse statue, was left at the gates of the City of Troy. But hidden inside that large gift were soldiers waiting to be “inside the gates”. Learning from that story, your mission is to make sure that your SAP Solution Manager does not become a “trojan horse”, delivering threat actors directly into your S/4HANA system!!
Think Logically – You have invested so much to protect your ECC and S/4HANA primary systems. Next, you set up approved Interfaces to connect Solution Manager to your primary systems… but then, you fail to protect that “other system” at the other end of the interface? That doesn’t make sense. Right? There is a “Chain of Custody” in play as data moves through the interface architecture. It is a Security Chain… and it is only as strong as its weakest link. We must make sure that the systems at both ends of an interface are protected and cyber-resilient.
Think about Public Impact – Risk of Damage to Reputation: If your company’s SAP systems are breached in any way, the public will not care how the sensitive data was obtained. The breach could occur directly on one of your mission-critical Transactional or Data Warehousing systems. But, for our focus in this article, realize that the breach could also originate in Solution Manager, resulting in malicious Lateral Movement to other SAP systems. The public will not care that your SAP S/4HANA system was secure… BUT the attacker used ANOTHER system (Solution Manager) to access to S/4HANA. The public PERCEPTION will simply be that your company’s SAP systems were breached.
What exactly is SAP Solution Manager?
💡 SAP Solution Manager is a single SAP system performing as a Management System for other SAP systems
SAP Solution Manager is the home for many separate management functions:
Beyond its original use for implementation support, monitoring, and administration, Solution Manager is also known for its Change and Request Management (ChaRM) solution for Transport Management.
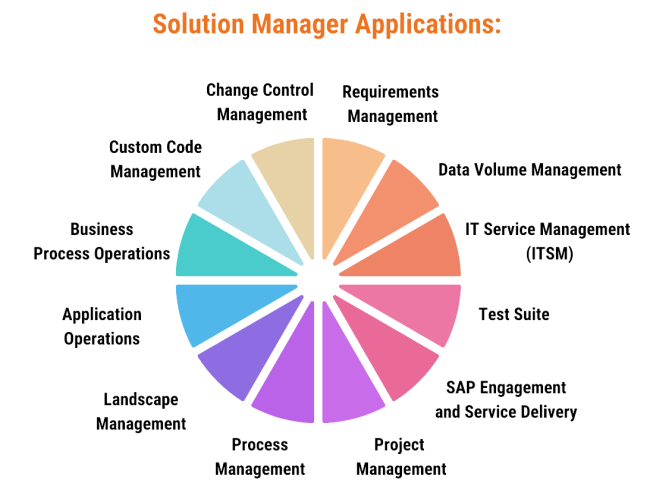
In fact, many “modules” or tools comprise the SAP Solution Manager suite of capabilities. Here are the Solution Manager applications from SAP Help:
- Business Process Operations – Your Basis team and Business Process Owners might use this application to look at job runtimes and document backlogs. They can also monitor performance, optimization, automation, and even data consistency… all with an eye toward an associated/impacted Business Process.
- Custom Code Management – Your ABAP Development team might use this capability to manage the full lifecycle of the Custom Code. This could also include Usage Logging by Usage and Procedure Logging (UPL) or its successor ABAP Call Monitor (SCMON). This logging might include information from managed systems where the usage logging from managed systems is extracted, relayed to the Solution Manager, and centrally stored in Solution Manager.
- Change Control Management – Your Dev team and Basis team might be utilizing this application for any of these capabilities: Change and Transport System (CTS), Transport Execution Analysis (TEA), Change Diagnostics, Central Change Transport System (cCTS), Quality Gate Management (QGM), Change Request Management, & Release Management.
- Requirements Management – This capability can be used as a stand-alone management application, or it can be integrated with SAP Project Planning and Management (PPM).
- Data Volume Management – Your SAP Basis Team and SAP Architects might use this application to supplement the overall Data Lifecycle Management for your company. Your company might also have a Data Governance Team, (or even a Chief Data Officer) that relies on this application. This application looks at the Data Volume on your managed systems with a data eye on: Monitoring, Analysis, Sizing, Forecasting, Compression, Archiving, Allocation, and Usage.
- IT Service Management (ITSM) – You might be running your internal “ticketing system” for SAP out of your Solman system. If it’s enabled, it could also be integrated directly into SAP for SAP vendor support tickets for your company. It could also be integrated with other SAP or 3rd party help desk ticketing systems.
- Test Suite – Solution Manager might be used to Administer and Operate Testing in your QA environments. (Your SAP Test Lead will know if this is the case.)
- SAP Engagement and Service Delivery – Utilized if your company engages with SAP Services.
- Project Management – integrates with SAP Best Practice packages.
- Process Management – connects solution documentation with project management and requirement management.
- Landscape Management – Your Basis team uses this capability to gather data from the existing SAP system landscape directory (SLD) along with agent data from the technical systems. This is collected into the Landscape Management Database (LMDB).
- Application Operations – comprises multiple sets of tools across the following categories (see link for more details):
– System and Application Monitoring
– Root Cause Analysis and Exception Management
– Technical Analytics and Dashboards
– Technical Administration
Why Protect SAP Solution Manager?
💡 If you run it, protect it! It’s 2024, not 2027... and not 2030.
I have interacted globally with hundreds of SAP consultants this year. We have discussed the SAP 2027/2030 deadlines from almost every angle possible. When it comes to Solution Manager (aka “Solman”), there are a couple of key thoughts:
- SAP has a product roadmap to help folks move to their replacement product(s): Cloud ALM and Focused Run.
- The need for a Solman migration does not receive anywhere near the amount of attention, budget, priority, and urgency as the larger S/4HANA transformation programs.
- One possibility is this migration topic: Solman–>Cloud ALM/Focused Run, might already be included in a major Cloud+Digital+S/4HANA Transformation Program. . .in this way, it becomes similar to a 1999 corporate initiative with many loosely related projects all lumped together under a massive “Y2K Program” (aka Year 2000). If you are young, you can study Y2K projects to catch up 😉.
- The other possibility is your SAP Enterprise Architects may choose to keep Solman through 2030 under SAP’s extended Maintenance.
- This allows for S/4HANA to be up and running and stabilized for a couple of additional years before the customer is forced to migrate from Solution Manager to Cloud ALM & Focused Run.
- This option would also give Cloud ALM (CALM) more time to mature since it is not yet as “feature-rich” as Solution Manager.
- Another possibility is that the SAP customer will replace the Solution Manager functions with point solutions from other vendors instead of SAP… yes, that is an open secret! There are other vendors in the SAP Change Management/Application Lifecycle Management (CM/ALM) market segments. Shhh!! 😉
- The final possibility is that your Solution Manager is sitting in a Blind Spot for Project Scoping. Reject the tendency to secure this last… on the reasoning that it is only an internal administrative system! Then it is forgotten — shoved to the back of the line… a faded entry on a long list of “digital transformation” priorities. With that thinking, it is left to be a perfect target for Cyber Attackers.
Depending on how your company will triage the SAP Solution Manager migration to ALM/Focused Run, you must plan to secure Solman at least through 2027, and possibly even through 2030. Additionally, find out if there are plans to introduce a 3rd party solution to replace the Solution Manager product. Not all SAP customers use ChaRM, for example, as their solution for Transport Management. So, even if you are not using ChaRM, you might be using Solution Manager for other mission-critical business processes.
What are the top Cyber Risks for Solution Manager?
💡 Lateral Movement into other systems via interfaces
Think like a Hacker – if you wanted to compromise the digital crown jewels of a company in SAP, you really don’t care what route of tunnels, back doors… or SIDE doors… you have to go through. The goal is to eventually get to the crown jewels and exfiltrate or otherwise compromise the data of the company under attack. Thinking like a hacker, you would use the most efficient means available to accomplish the exploit. (unless you want to MAKE it look messy, of course… but that is a topic for another day). If Solution Manager is part of the most efficient vulnerability exploit strategy, then Lateral Movement will be the most commonly attempted technique.
💡 Solution Manager contains the “inventory” of all your SAP landscapes and systems.
Think like a Hacker – where would you go if you wanted to learn a full inventory of all the potential hack targets of a customer’s SAP systems? SAP Solution Manager! All the other SAP systems are named there… and even the interfaces are there for you to browse or even to test the connections!
💡 Solution Manager Diagnostics (SMD) can deploy an “Agent” (SMD Agent) on every SAP system.
Think like a Hacker – What if that SMD Agent could be compromised in some way? You could own every SAP system in the customer’s SAP landscapes. Oh, yeah. Forgot to tell you one thing. This has already been researched and reported to SAP. SAP has closed off this exploit capability. But did your company deploy the necessary patches to close it off in YOUR environment??
How can I protect SAP Solution Manager?
💡 Check the core: SAP NetWeaver AS JAVA and ABAP
Solution Manager is at risk of vulnerabilities and exploits in 2 major technology stacks. This is because the deployment configuration of Solution Manager utilizes what is called a Split Stack architecture (a 2-SID approach utilized for Solution Manager and another SAP product for interface traffic called Process Integration or PI).
We are all long since gone from the old “Dual Stack” architecture, right?? But for the “Split Stack” architecture, you must protect both a Java SID as well as an ABAP SID! Whether it is Solution Manager or Process Integration (PI) systems, remember to protect BOTH SIDs in the split stack architecture.
I recommend the scanning and monitoring solution from SecurityBridge for Split Stack environments. SecurityBridge can perform security& compliance checks and monitor for exploit actions on both SAP NetWeaver AS Java and SAP NetWeaver AS ABAP systems.
Also, you can utilize SecurityBridge Patch Management to make sure that BOTH systems in the split stack are up-to-date on their SAP Security Notes. The Patch Management will scan one SID in the ABAP context and the other SID in the Java context.
💡 Solution Manager has some unique architecture that requires specific SAP CyberSecurity protection
SecurityBridge can make your Solution Manager system more Cyber-Resilient. Solution Manager serves some very specific, strategic, and sensitive functions in your SAP ecosystem. This server is truly unique in purpose from other SAP systems:
✔️ Check for Missing SAP Security Notes that are specific to Solution Manager
Utilize the SecurityBridge Patch Management capabilities for Solution Manager to make sure that all the SAP Security Notes that are specific to SAP Solution Manager components are checked and confirmed to be installed.
✔️ Check for Sensitive Access via Combinations of Authorization Objects that are unique to Solution Manager Roles
If your Basis Team uses Solution Manager to configure other SAP systems, then the Solution Manager system will have User/Role/Authorization combinations not commonly found on any other SAP system. Check the Solution Manager Security Configuration Guide for more details on this topic. https://help.sap.com/doc/b4a8c8e4d575476ba67bdbf69a904b24/7.2.08/en-US/SecConfigGuide.pdf
Your SAP Cybersecurity Solution must be able to analyze these combinations of Authorization Objects in the scanning and monitoring options. SecurityBridge supports these options for Solution Manager’s sensitive use of Authorization Objects.
✔️ Check for the consistent update of Solution Manager Diagnostics Agents (SMD Agent) with Solution Manager
A monitoring agent on a server can be a great thing… unless it becomes the unwitting “inside man” … the inside launch point of a vulnerability attack. This was the case for the SMD Agent a few years ago. For those SAP environments that have an SMD agent deployed, take special care to ensure that each of those systems is patched for the vulnerability that was found in the SMD Agent architecture. Reference these advisories from 2020 to understand more about that piece of Solution Manager history…
https://www.abex.io/advisory/detail/2890213
https://www.abex.io/advisory/detail/2845377
…and make sure that history does not repeat itself in YOUR environments.
Double-check this SAP KBA for any system with an SMD Agent deployed onto it: https://me.sap.com/notes/1931100 !! 😉
✔️ Utilize a second check on your Transport Security
Whether you utilize ChaRM for Transport Management or you have some other solution, you should know that you can also utilize the SecurityBridge Transport Scan capability to scan the code inside those transport requests. Remember that “Transports” are technically just a collection of SAP ABAP Code that has been bundled into a task request and then further into transport requests. Think of these as container objects for the ABAP Code that is being sent to another system or client destination.
Here is a helpful description from the SecurityBridge Customer Knowledge base: “Every SAP transport is designed to create a change in the destination system. Minimizing or even eliminating the risk of transport deployment issues is very important, not just because rolling back might be quite cumbersome. The SecurityBridge Transport Security enables SAP administrators to scan transport requests even before the import occurs. SecurityBridge Transport Security allows scanning of external transports from file or import directory, highlighting potential security flaws, even within code not yet imported.”
✔️ Protect your SAP Server Inventory - Monitor when the SAP environment data is accessed on Solution Manager
The combined collection of the metadata from all other SAP systems in your shop creates a higher level of sensitivity and risk in this unique set of data. This data must be protected from those who might try to exploit the rest of your SAP systems by using this information as a navigation map of your SAP ecosystem.
Concluding Thoughts
- Do not neglect Solution Manager in your SAP Cybersecurity Scoping and Planning discussions.
- Solution Manager “HAS CONNECTIONS” — It is connected to almost every other SAP system in your SAP landscapes.
- Solution Manager collects and maintains sensitive information about the SAP servers throughout your SAP Enterprise Architecture.
- Include a Solution Architect from SecurityBridge to help you on this important mission!
- Solution Manager still needs efficient management of the SAP Security Notes monthly cycle of updates. The solution architecture should include SecurityBridge Patch Management.
- Solution Manager has unique technical capabilities not found in other SAP environments. The solution architecture should include SecurityBridge Vulnerability Management, Interface Traffic Monitoring, and Threat Detection Capabilities.
References:
- SAP Support – Transition Guidance: Solution Manager to SAP Cloud ALM https://support.sap.com/en/alm/sap-cloud-alm/transition-to-sap-cloud-alm.html
- SAP HELP for Solution Manager https://help.sap.com/docs/SAP_Solution_Manager
- SAP NetWeaver 7.5 End of Maintenance 2027/2030 – SAP Product Availability Matrix (PAM) https://apps.support.sap.com/sap/support/pam?hash=pvnr%3D73554900100900000414
- End of Maintenance for NetWeaver 7.5 (and products that rely on NetWeaver 7.5) explained for SAP Community and SAPinsider:
- Blog Series – What is the right SAP ALM solution for me (Solution Manager or SAP Cloud ALM): https://community.sap.com/t5/technology-blogs-by-sap/alm-for-sap-s-4hana-cloud-sap-cloud-alm-or-sap-solution-manager/ba-p/13541560