SecurityBridge
covers 250+ attack patterns.
Detects and reports on system attacks and other suspicious activity in real-time.
We use the capabilities of machine-based detection patterns to assess all relevant SAP data sources. In addition to standard log sources, such as the Security Audit Log or System Log, there are numerous other data sources needed to evaluate whether a vulnerability has been exploited.
SecurityBridge for SAP© automatically utilizes all of this information to add context to security events. As result, such events can be read and evaluated by Security Analysts, even without expert SAP knowledge.
Protect your assets and secrets!
More than 25 relevant security log sources.
We use the capabilities of machine-based detection patterns to assess all relevant SAP data sources. In addition to standard log sources, such as the Security Audit Log or System Log, there are numerous other data sources needed to evaluate whether a vulnerability has been exploited. SAP-based systems are the host for many of your business-critical processes. SAP FI holds bank account information, payment data and much more. SAP ERP and CRM contain business partner address details, purchase history and forecasts. SAP HR is again home for personal data of your workforce. SAP SRM systems store details about RfPs, contract bidding, supplier information, vendor negotiation results, etc. Such sensitive information should not be exposed to unauthorized parties.
Detecting such a wide range of potential threats against critical business processes and data cannot be achieved by monitoring a single log. Without enough information, critical actions may go unnoticed. Sensitive data, which could impact the business success or brand image, may land on a USB-stick. A denial-of-service attack or a lock attack could disrupt business processes or even trigger an entire system outage.
Industrial espionage targets trade secrets, which may result in a dramatic financial and reputation loss. The history of SAP attacks proves that even amateur hacking attempts can result in full outages and bankruptcy of firms. SecurityBridge for SAP® applications enables companies to react and neutralize incidents before they escalate.
Log Crawling
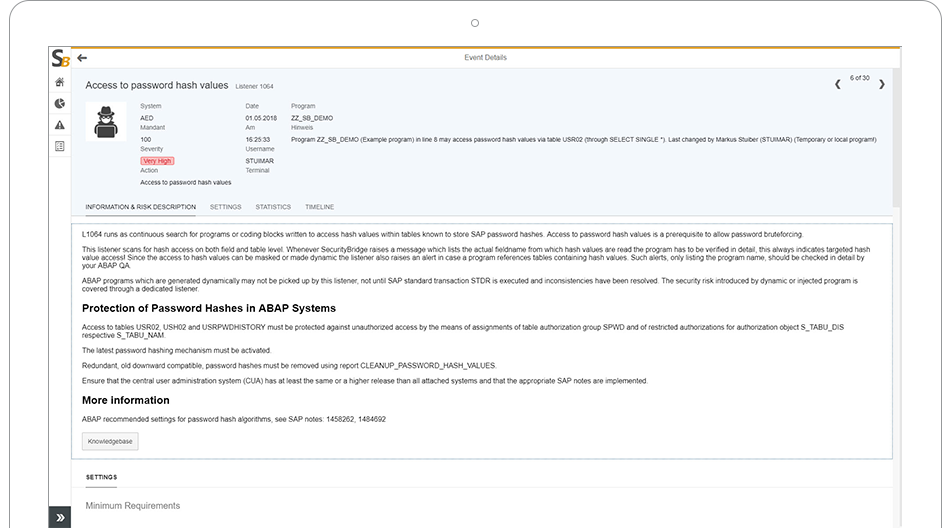
The SecurityBridge Intrusion Detection Scanner (IDS) continuously reads all SAP logs to measure the security state of the system. For each event identified, the IDS algorithm decides on the security relevance, and assigns a severity rating, using the common vulnerability scoring system (CVSS). Alert messages are enriched with the context required to make the event actionable. Some of the primary log sources processed in real-time:
Table Logs
Description
The standard SAP system will not record changes users make directly to a table using transaction SM30, or if a developer writes a program directly changing table contents. Table logging is a track mechanism that records table content changes in a system. It is useful if you want to know: Who made a change? What was changed? When was the change made?
Priority
High
Classification
Manual activation needed! Customer specific tables require the table logging attribute to be set.
Storage
SAP DB
Change Documents
Description
Business data is changed frequently. These changes can be logged for objects that are critical or susceptible to audits. It is helpful, and sometimes necessary, to trace or reconstruct such changes during an investigation or system audit.
Priority
High
Classification
Active by default. Customer specific enhancements are possible.
Storage
SAP DB
User Statistics
Description
The Business Transaction Analysis (Transaction STAD) delivers workload statistics across business transactions. Any program or transaction executed is recorded. Many systems only store statistical information for a short duration.
Priority
Very High
Classification
Active, by default
Storage
SAP DB
Security Audit Log
Description
The Security Audit Log is the primary source for security and audit relevant events in any SAP system.
Priority
Very High
Classification
Manual activation needed!
Storage
DB, File or both
(Note 2191612)
HANA Security Log
Description
This section is only relevante to HANA based systems. Other DB systems may contain their own security and audit log.
Priority
High
Classification
Manual activation needed!
Storage
SAP DB or filesystem
System Log
Description
The SAP System Log includes all system errors, warnings, user locks due to failed logon attempts from known users, and process messages in the system log.
Priority
High
Classification
Manual activation needed!
Storage
Filesystem
SAP Logging
Enable the logs!
More than 70 identification algorithms (so-called SecurityBridge Listeners), covering hundreds of possible SAP attack vectors are shipped and configured out-of-the-box with SecurityBridge.
If attack or exploit signals (or anomalies) are identified, the applicable listener will immediately evaluate the environment to collect all relevant information and evidence for a detailed alert.
By combining intelligence, which SecurityBridge reads from Change Documents, the Security Audit Log, the System Log, Gateway Logs, the System Process Overview and more, it is now possible to detect threats near real-time.
Since SecurityBridge natively runs within the SAP application stack, there is no need to harvest and extract gigabytes of logs. Log assessment and correlation runs entirely within your existing SAP landscape.