Hyperlogging – to boldly go where no one has gone before

Whenever Captain James Tiberius Kirk encounters an anomaly in the famous TV-Show “Star Trek”, he quickly assembles a landing team to investigate the anomaly further on the planet it sprung up. If the anomaly appears somewhere in space, Kirk would send a probe. What is the relation to SAP security, you may wonder? Well, if you want to know whether an anomaly you detected represents a harmless activity or a security breach, you need two things: more details and more data. To gather both, we have introduced what we call “HyperLogging” as a new feature in SecurityBridge.
How does HyperLogging for SAP work?
Think back to Captain Kirk and Star Trek. If they send a probe to investigate an anomaly in outer space, this probe is packed with sensors and instruments which can read details and data that could not be collected using the so-called “long-range” sensors the Starship Enterprise usually uses. Similarly, when gathering a landing team, Kirk usually employs “Pill”, the doctor – to collect medical data, if applicable; Spock, the science officer – for the scientific details, and so forth. With HyperLogging, we introduce the same capability for SAP endpoints. The Intrusion Detection Scanner instructs the agents which run on every SAP system to collect all possible data from any endpoints, such as terminals. This includes basic data such as IP address and technical details of the terminal, but also specific data such as change documents, called transactions or function modules.
Obviously, this data as such will only make sense when analyzed and correlated to other data from that terminal but also from the entire system landscape. Therefore the collected data is sent to the central controller of SecurityBridge where it can be analyzed for SAP specific attack patterns.
What makes HyperLogging different?
What makes hyperlogging fundamentally different from probes and landing teams in Star Trek, however, is also one of its best features: it will be enabled automatically. Captain Kirk and his crew need to discuss the anomaly first and only then send a landing team, which costs precious time, at least in an SAP security context. With hyperlogging enabled, whenever a preconfigured event occurs, the IDS will automatically launch a probe, to stay within the Star Trek analogy. This could be a critical account logon or a specific function module which is executed. When such an event is triggered, hyperlogging will be activated immediately, logging all available data from the terminal or server in question. Which data is logged and for how long can also be customized. Which leads us directly to the next feature.
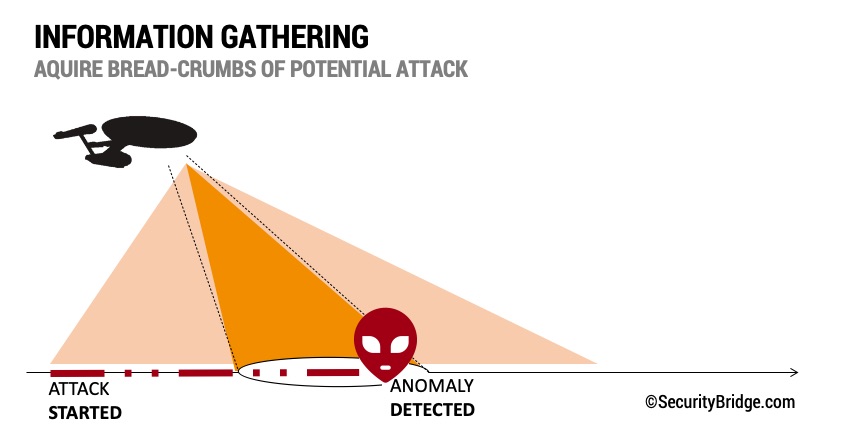
Look back in time
before an anomaly was detected
Do you also think that those Star Trek episodes, which involve time travel are the best episodes? We certainly do, although this is not the only reason why we added time travel to HyperLogging.
While we admittedly failed in achieving what generations of scientists (and science fiction authors) have longed for, hyperlogging does let you travel back in time. Once the HyperLogging feature gets activated SecurityBridge will not only start collecting data going forward, it will also retrieve those sets of data that have already been logged. As an added benefit, all this data will also be stored redundantly within the SecurityBridge platform.
This additional data will help in quickly identifying a potential threat through the SecurityBridge correlation engine. If the threat cannot be narrowed down immediately, that additional data will also be helpful in forensic research after the actual threat has occurred. The combination of “historical” data-sets with data that is being written, while the attack is going on, will also help SecurityBridge to learn and improve the alerting for a similar attack in the future.
In other words, by enabling the HyperLogging feature of SecurityBridge, the 360° insight into your SAP security posture will be even more comprehensive than before. The only thing you’ll be missing is the famous Star Trek quote after the landing team has finished collecting data: “Beam me up, Scotty”.
SecurityBridge is a modern SAP Security Platform, natively build in SAP. It uses an ABAP based Intrusion Detection System (IDS) to guard your SAP landscape 24/7. Its frontend is build with Fiori, which provides you an intelligent insight on the security posture of your ABAP, Java and HANA based systems.
Seeking for more information on HyperLogging? Don’t hesitate to reach out. We are happy to answer your questions.
HyperLogging Product Page
Looking into securing your SAP landscape? This white-paper tells you the “Top Mistakes to Avoid in SAP Security“. Download it now.