Home /
Security News
Articles sharing relevant insights into security news, operations, recent incidents and data breaches but also provide guidance for SAP running enterprises.
The Art of SAP Security...
100% security just doesn’t exist. Any security measures taken will not be perfect, ever, and will require continuous adjustment. Ignoring security for SAP is not an option, it’s merely applying due diligence to any company’s most valuable, and essential core business.
Read MoreWhy normalize and automate SAP audits?...
Auditors are digging into SAP in more detail, asking questions about the secure configuration of SAP and the use of critical standard profiles, beyond the known SAP_ALL authorization profile.
Read MoreIBM QRadar Security Intelligence...
IBM QRadar provides an adapter for the distinct purpose of connecting with RESTful APIs. Using SecurityBridge you can turn your SAP instances into a smart security event provider to turn the enterprise-critical application into a white box for your SOC team.
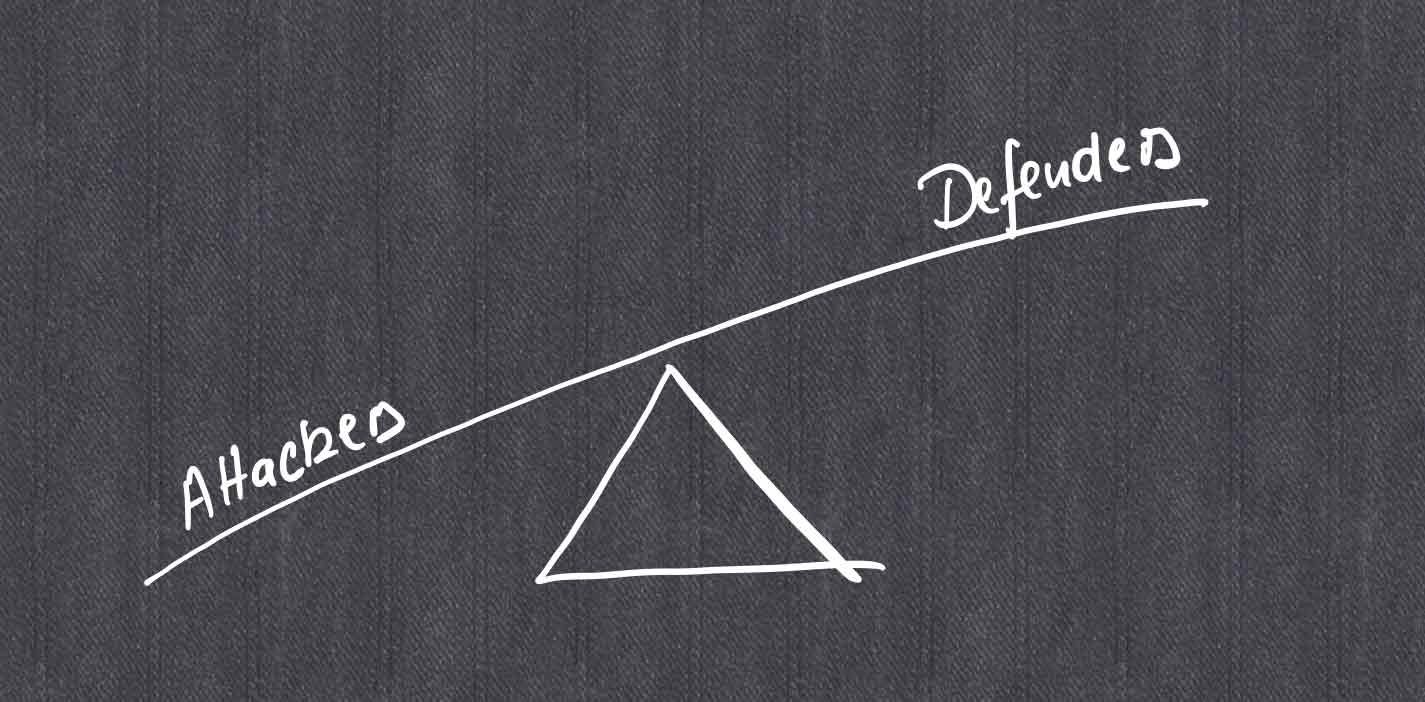
Read MoreThe asymmetry between attackers and defenders...
Complex, enterprise-critical systems, are not secure by design, and by default. Defenders must put in an effort, usually manual, to maintain and build a secure configuration. Once accomplished, the security posture needs to be maintained, continuously and long-term, while the system is subject to frequent change and version updates.
Read More3 Reasons to start monitoring SAP...
There appears to be a new trend for companies to centralize their log sources into Security Information and Event Management (SIEM) solutions. The time has come to look at SAP. This article explains why.
Read MoreVirtual patching – especially attractive to SAP...
SAP systems belong to the companies’ critical infrastructures, no doubt. Yet, enterprises struggle with the timely implementation of patches. Within this article, we provide a deep-dive into the challenges that let you remember how patching SAP NetWeaver application works.
Read MoreWhy CISA strongly recommends monitoring SAP?...
The Cybersecurity and Infrastructure Security Agency (CISA) strongly recommends organizations immediately apply patches, and in situations where patches cannot be applied, CISA recommends “closely monitoring your SAP NetWeaver AS for anomalous activity”.
Read MoreThe week after SAP RECON [CVE-2020-6287]...
SAP Patch Day July 2020 shocked the customer community of SAP SE. Although everyone assumed that zero-days with a high-risk potential of exploitation exist, the recent Patch Day has delivered evidence. Read more to understand what you should do as the next best action to protect your enterprise.
Read More2FA for SAP, and how to hack...
Gear up your SAP Logon process using 2 factor authentification. 2FA, typically demands two components to co-exist, in the same place, at the time of login. In practice, this typically means the end-user has a physical device such as a SmartCard, and a memorized PIN number.
Read More







![The week after SAP RECON <br> [CVE-2020-6287]](https://securitybridge.com/wp-content/uploads/2020/07/blog-cve-2020-6287.jpg)
