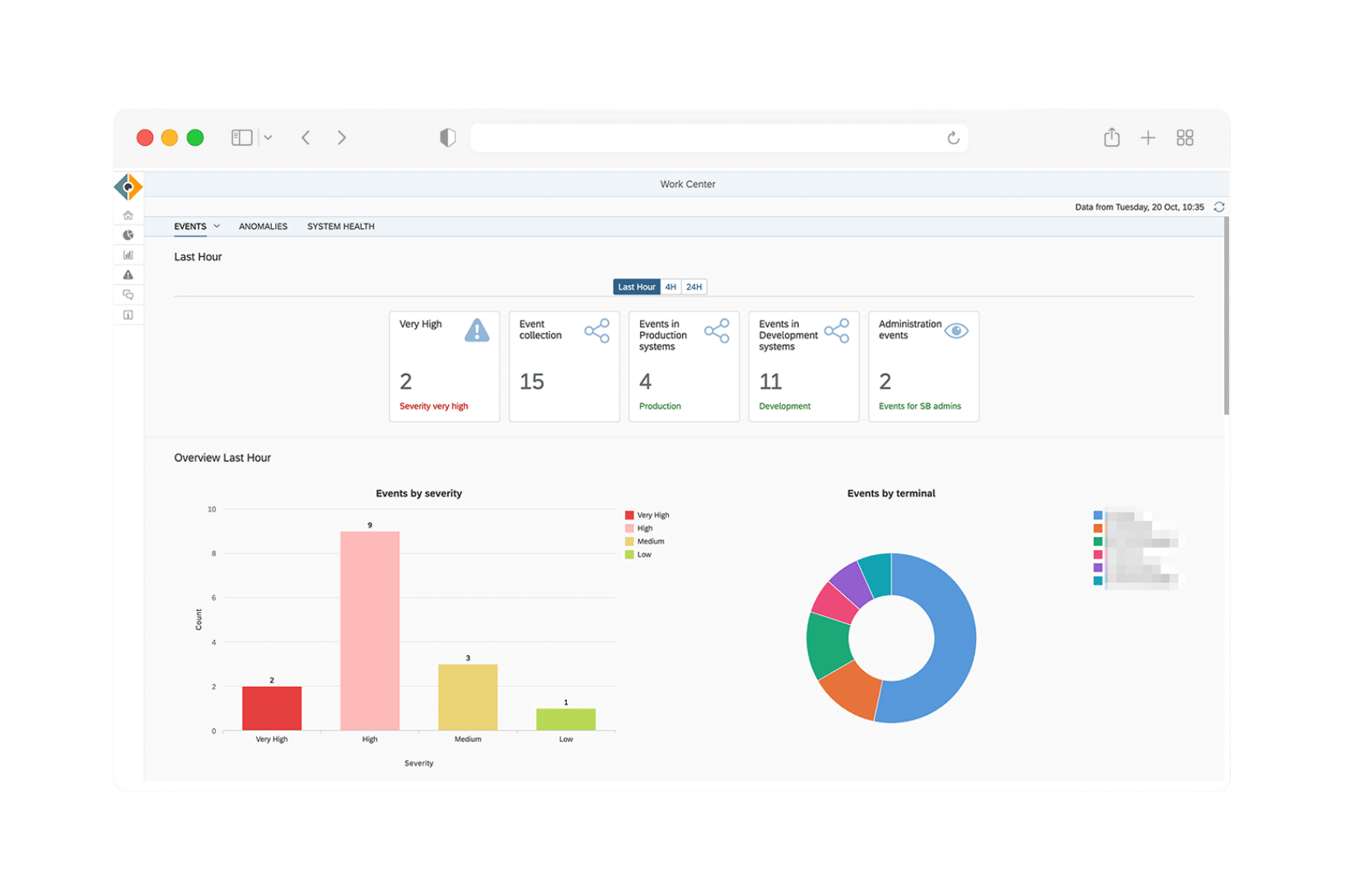
Integrating Privileged Access Management into the SecurityBridge SAP Platform
The inclusion of Privileged Access Management PAM in our platform marks a significant advancement for existing and future customers Until now our focus was primarily on monitoring and detection With PAM the platform extends its capabilities to grant manage and audit privileged access in SAP 8217 s ABAP 4 based products Looking ahead we plan to expand this functionality to include JAVA based SAP products too