Blog - SAP Security Key Insights
- Careers
- Download assets
- Events
- Life at SecurityBridge
- Our Partner Network
- Press coverage
- Product Feature
- Release highlights
- SAP Cloud Security
- SAP Code Security
- SAP Cybersecurity
- SAP Identity and Authorization
- SAP Interface
- SAP Patch Day
- SAP Patch Management
- SAP Security Automation
- SAP Security Framework
- SAP Security Logs
- SAP Security Patch Day
- SAP Threat Monitoring
- SAP Vulnerability
- Security News
- Uncategorized
What is the SAP cyber risk...
What is cyber risk appetite? Businesses must be more cautious to protect themselves from
Read MoreThe three most common types of...
3 most common types of SAP Patches Installing SAP patches is crucial for maintaining
Read More5 Tips to ensure SAP Interfaces...
5 Tips to ensure your SAP Interfaces are secure Security has become increasingly important
Read MoreSAP Security Patch Day – January...
As we start the New Year, it is important for organizations to make sure
Read MoreSAP Security Patch Day – December...
Today, December 13rd, 2022, is another day for SAP to release security updates for
Read MoreGame changer: Managed SAP Security Services...
Managed SAP Security Services: A game changer The increased risk of being exploited and
Read MoreSecurityBridge Releases New One-Click SAP Patch...
< Back to Overview Ingolstadt, Germany, November 16, 2022 – SAP security provider SecurityBridge—now
Read MoreIT-SiG 2.0 – Angriffserkennung für SAP...
Viele unserer Leserinnen und Leser erinnern sich noch an den 25. Mai 2018, Stichtag
Read MoreExternal vs. Internal SAP Cybersecurity Risks:...
The difference between internal and external sap attackers Recently, we gave an insight into
Read MoreSAP Security Patch Day – November...
< Back to Overview Today, November 8th, 2022, SAP releases security fixes for their
Read MoreSAP Business Technology Platform (SAP BTP)...
Inspired by the many conversations we had at this year's DSAG Annual Congress 2022,
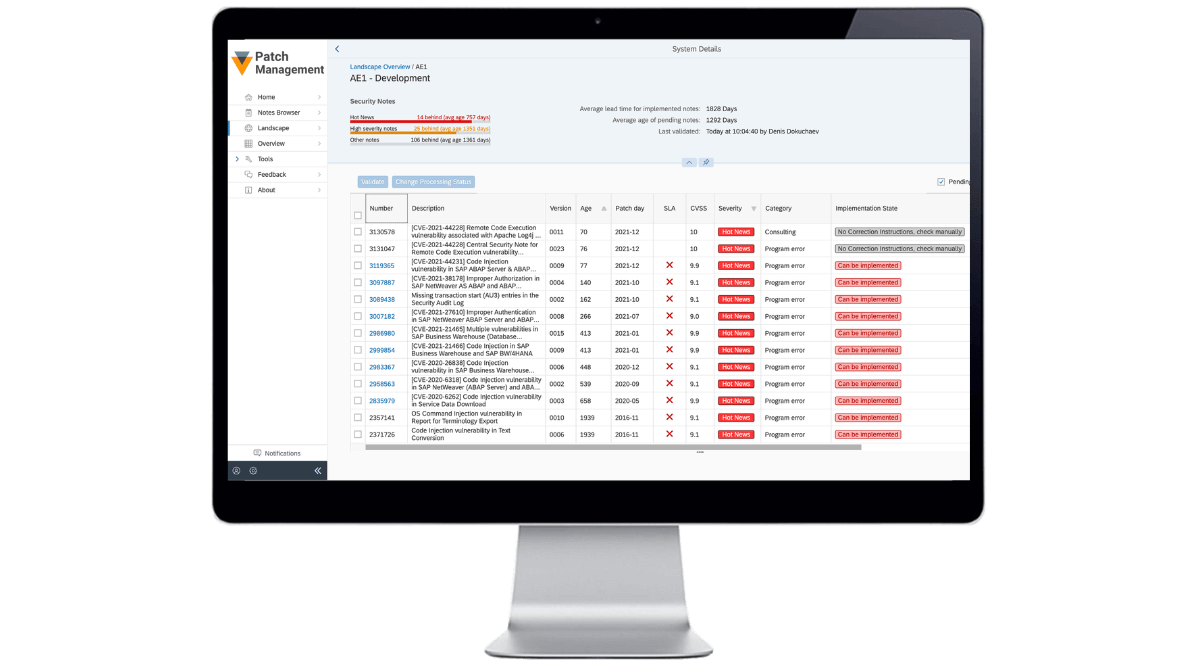
Read MoreThe difference between SAP Patch Management...
SAP Patch Management and vulnerability management: The difference Believe it or not, I've probably
Read MoreSAP Security Patch Day – October...
< Back to Overview October 11th is not only the monthly SAP Security Patch
Read MoreSAP Security Dashboard...
The SAP Security Dashboard Whether security in SAP environments is relevant is not up
Read MoreHow to master SAP code vulnerabilities...
After reading the title, you're probably thinking - Why should legacy code be handled
Read More